Case Study | 29 July 2025
How a Blockchain Security Firm Bolstered Its Infrastructure After a Smart Contract Exploit Incident
Posted by : Akshay Pardeshi
A single security lapse can damage years of trust, especially in the high-risk, high-speed world of DeFi and blockchain. In late 2021, a prominent blockchain security firm, highly known for auditing smart contracts and tracking crypto transactions, faced this reality firsthand. The fallout was swift; it hampered the client's confidence, caused reputational damage, and raised questions about the firm’s long-standing credibility. Thus, in response, the company reached out to Research Nester for expert guidance to redefine its infrastructure and future-proof its security practices. What emerged was more than just a fix; it was a complete strategic transformation.

An overview:
Established in 2015, the enterprise had rapidly gained popularity as a key player in blockchain security, by offering smart contract auditing, DApp testing, and blockchain transaction monitoring solutions. With collaborations across DeFi platforms and Layer-1 blockchain service providers, the company established itself as a reliable company in the Web3 ecosystem. However, in late 2021, the company became the target of a high-impact system breach where a client’s decentralized finance (DeFi) platform, recently audited by the firm, incurred a $14 million financial loss due to a smart contract issue that was missed during the security check. The event degraded not only the client’s financial standing but also called into question the integrity of the security firm’s audit processes.
Negative press, investor mistrust, and reputational risk hit the company hard. Its reliability was now under international oversight. In a bid to regain credibility and overhaul its audit and monitoring protocols, the company partnered with Research Nester to receive strategic consulting and software infrastructure guidance for improved smart contract security and real-time threat detection.


The Story
As a leader in blockchain security, the company had built its reputation on precision audits and in-depth penetration testing. Over the years, it has served nearly 400 clients globally, including decentralized finance (DeFi) protocols, NFT platforms, and Layer-2 scaling solutions. Its reports were often quoted in investor pitch decks, and its security badge on a DeFi platform often represented user confidence. In November 2021, the company faced a major setback. A DeFi yield farming protocol that it audited just three weeks earlier was exploited via a reentrancy loophole. The attacker extracted $14 million in stablecoins within minutes. Blockchain explorers flagged the suspicious transactions, and within hours, the incident resulted in widespread outrage on Twitter.
Although the exploitation took place in the client’s smart contract, the fact that the firm’s audit was not able to detect the vulnerability raised serious scrutiny. Prominent crypto influencers questioned the firm's auditing methodology, while competing firms used the opportunity to position themselves as more comprehensive and detail-oriented, leading to a loss of customer base.
Within a week, three other DeFi protocols terminated their audit agreements with the company, citing a loss of confidence. The company, understanding the long-term damage this could have, decided to act quickly. To ensure this incident would never repeat, and to reassure both existing and potential clients, it reached out to Research Nester, a global strategy consultancy known for its deep market research in cybersecurity and emerging technologies. After an initial assessment, Research Nester consultants noted the following shortcomings in the company’s existing infrastructure and processes. A few of them are mentioned as follows:
- Obsolete audit checklists: The company was using a generalized, outdated audit checklist that had not been updated with new DeFi threats such as flash loan attacks, sandwich trading, and oracle manipulation.
- Manual dependency: Excessive dependence on manual code reviews caused higher cases of human errors in the process. There was a lack of standardized automated tools that could test complex multi-contract interactions.
- Lack of real-time tracking: Post-audit, there were no mechanisms in place for real-time smart contract behavior monitoring.
- Infrequent threat intelligence updates: The internal knowledge base on exploit patterns was being updated only quarterly, making it very slow to adapt to new threat vectors.
Our Solution:
Research Nester analysts and technical experts delivered a multi-tiered strategic roadmap, which the blockchain security company adopted over the next 12 months. The solution included a fusion of advanced technological integration, process overhaul, and staff upskilling:
- Smart contract vulnerability detection suite: A custom vulnerability scanning engine was developed using dynamic analysis tools. It included:
- Symbolic execution engines to simulate smart contract behavior.
- Integration of Mythril, Slither, and Manticore into a single interface.
- AI-powered code analysis was used to identify high-risk functions and detect anti-patterns throughout the codebase.
This significantly reduced manual effort while increasing the depth and breadth of each audit.
- Exploit pattern intelligence repository: Research Nester helped form a Threat Pattern Repository (TPR), a dynamic knowledge base that:
- Regularly syncs with open-source security alerts.
- Analyzes historical exploit data to form new heuristics.
- Supports predictive modeling using graph-based blockchain analysis.
This helped the company stay ahead of attack trends.
- Post-audit behavioral monitoring system: A new SaaS offering, ChainGuard Sentinel, was launched, allowing clients to subscribe to on-time monitoring of used contracts. It featured:
- Gas usage anomaly detection.
- Transaction pattern assessment using AI and ML models.
- Triggers alerts on anomalous external calls and unauthorized proxy upgrades.
This additional layer gave clients greater peace of mind post-deployment.
- Quarterly training and war room simulations:
- Engineers and analysts were put through war room simulations, practical, timed exercises using past DeFi exploits.
- Quarterly sessions involved reverse-engineering attack scripts, stress-testing smart contracts, and modernizing risk classification models.
This initiative formed a culture of continuous learning and agility.

Results
The company’s infrastructure overhaul and internal process reforms resulted in measurable gains in both market trust and client outcomes.
- Reputation rebound: Within just six months of the strategic partnership, the firm successfully resecured audit contracts from five major DeFi platforms, including three that had previously cut ties. A newly launched security badge, supported by ChainGuard Sentinel’s post-audit monitoring, arose as a key differentiator in gaining back trust.
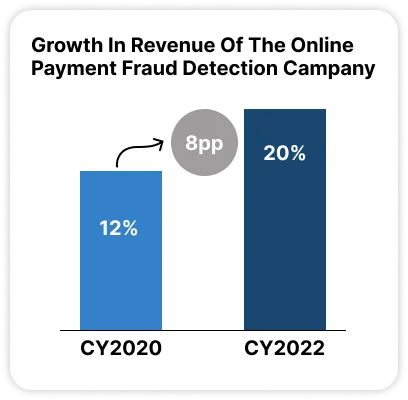
- Revenue growth: Revenue jumped from 8% YoY growth in 2021 to 21% by 2023, driven by a rise in the adoption of ChainGuard Sentinel subscriptions and premium audit services.
- Client trust regained: Client satisfaction scores went up by 38%, showing renewed confidence in the company’s offerings. In 2023, nearly 85% of new clients mentioned that improved technical capabilities and higher transparency as the primary reasons for choosing the firm over its competitors.
- Zero exploitation reported: No major exploits were noted across any client platforms audited under the new system, solidifying the firm’s rebranding narrative.
- Industry thought leadership: The company strengthened its place as a security leader by highly contributing to the Ethereum Foundation’s research initiatives. In 2024, it open-sourced two of its owned audit frameworks, an initiative that increased its brand credibility and industry influence.
Conclusion
This case reflects the paradox that even security companies are susceptible to lapses in their infrastructure or processes. The blockchain security company's journey from being discredited after a smart contract exploit to becoming a market leader again reflects the reality of proactive, research-driven, and tech-forward strategies in cybersecurity. With the help of Research Nester, the company not only recovered from reputational damage but turned its biggest crisis into a driver for growth, innovation, and market differentiation.
customized message

Akshay Pardeshi is an accomplished Senior Research Analyst at Research Nester, with over 6 years of experience driving strategy, innovation, and client success across niche industrial domains. His sectoral expertise spans IT & Telecom (cloud technologies, cybersecurity, AI, IoT, 5G infrastructure), Electronics & Smart Devices (consumer electronics, smart home systems, wearables, semiconductors), and BFSI & Allied Services (digital banking, fintech, insurance tech, and IT services).
Akshay specializes in translating complex data into clear, actionable intelligence that informs strategic decision-making. His expertise spans competitive intelligence, market sizing, industry and customer research, trend analysis, and strategic forecasting. He is widely recognized for his rigorous research approach, structured analytical thinking, and ability to deliver high-impact insights that directly support business strategy and growth initiatives.
Akshay holds a Bachelor’s degree in Electronics, which provides a strong scientific and analytical foundation for his work. Throughout his career, he has demonstrated a consistent focus on accuracy, depth of insight, and client-centric delivery. In addition to his analytical strengths, he is highly skilled in project management and team leadership, enabling him to manage complex research engagements efficiently while ensuring timely, high-quality outcomes for stakeholders.
Thank you for contacting us!
We have received your request for proposal. Our research representative will contact you shortly.
Copyright @ 2026 Research Nester. All Rights Reserved.

